4 minutes, 52 seconds
Why upgrade?
 After watching my shopmate get one, then seeing The Wirecutter recommend it (as of May 2016) and then seeing Dell upgrade it, I was very tempted to get a Dell XPS 13 and run Linux on it.
After watching my shopmate get one, then seeing The Wirecutter recommend it (as of May 2016) and then seeing Dell upgrade it, I was very tempted to get a Dell XPS 13 and run Linux on it.
The straw that broke the camel’s back was seeing factory refurbished ones with 16GB of RAM, 512GB of disk, an i7, a Dell 1 year warranty and that gorgeous QHD+ resolution (3200×1800) for less than $1,300 on eBay (again as of May 2016). This is is about $700 off of retail for a comparably equipped machine (or a lot more). Though this ships with Windows 10, I figured I could install Ubuntu on it.
Ubuntu 16.04 install
 Before pulling the trigger on eBay, I did a lot of reading on the forums about how to install over windows. Specifically, posts like this we’re key. I knew in the BIOS that I needed to turn off Secure boot and switch disk mode to AHCI. Further reading suggested that it might be a real uphill battle to get everything, hardware wise, working.
Before pulling the trigger on eBay, I did a lot of reading on the forums about how to install over windows. Specifically, posts like this we’re key. I knew in the BIOS that I needed to turn off Secure boot and switch disk mode to AHCI. Further reading suggested that it might be a real uphill battle to get everything, hardware wise, working.
I’m happy to report that just about everything works under 16.04! I installed it after making an install image after USB boot drive from the .iso. The touch screen doesn’t work after suspend. I was hopeful that the xinput enable/disable trick might fix it, but no such luck just yet. Given that you can’t do single finger scroll and pinch to zoom when touch is working, I’m not too bummed about this.
I was very pleased to see that this cheap USB-C to DisplayPort adapter works great. Though it can’t quite do 4k (resolution shows in “Displays”, but my Dell won’t show an image), it will do all resolutions below that. It works on boot and after repeated hot swaps. The cheap USB to Ethernet adapter worked flawlessly as well, Handy times!
The other pleasant surprise was that the Broadcom WiFi/Bluetooth card also seems to just work under 16.04. Admittedly, I’ve just been using the WiFi with no problems and haven’t tested the Bluetooth.
The trackpad works as well as my MacBook Air trackpad did under 14.04. It looks like there’s some PS/2 vs Native twiddling that might improve palm detection, but I’m happy with it as is given it’s status quo for me.
Software and eBay
 There’s a little hiccup with OwnCloud resetting after suspend or WiFi hopping, but this is nothing to do with the XPS 13, and everything to do with 16.04. As well, the version of KeepassX that ships with 16.04 no longer supports the old version 1 flavor of the password safe. It was high time I upgraded to version 2 anyway!
There’s a little hiccup with OwnCloud resetting after suspend or WiFi hopping, but this is nothing to do with the XPS 13, and everything to do with 16.04. As well, the version of KeepassX that ships with 16.04 no longer supports the old version 1 flavor of the password safe. It was high time I upgraded to version 2 anyway!
Finally, anyone want to buy an 11″ Air formerly running Ubuntu 14.04, but now with a clean install of El Capitan?
6/2/2016 Update
 After having this laptop for a bit now and having made a few tweaks, I wanted to update this post. The first, and most important, change is that I found the Broadcom chip I mentioned above did not “just work”. Though strictly anecdotal, I found that the card had intermittent high packet loss on WiFi and was actually unusable when I went to use my Bluetooth mouse for a few hours. Swapping out the card it shipped with for the Intel 7265 802.11ac one, instantly solved all these problems. The Intal card may have caused WiFi to stop working just once after a bunch of suspend and resumes, but I can’t remember so it must not be that annoying ;)
After having this laptop for a bit now and having made a few tweaks, I wanted to update this post. The first, and most important, change is that I found the Broadcom chip I mentioned above did not “just work”. Though strictly anecdotal, I found that the card had intermittent high packet loss on WiFi and was actually unusable when I went to use my Bluetooth mouse for a few hours. Swapping out the card it shipped with for the Intel 7265 802.11ac one, instantly solved all these problems. The Intal card may have caused WiFi to stop working just once after a bunch of suspend and resumes, but I can’t remember so it must not be that annoying ;)
Two notes on replacing the card: The first is that while the Amazon link cited for this is certainly the right price at $20.99 (as of Jun 6 ’16), it is a bit slow in shipping. The second is that you should totally use iFixit’s XPS 13 tear down guide as a how to for opening this laptop. As well, they cite the online Dell repair manual (pdf), if you want to reference that. And, yes, when iFixit says the bottom of the laptop takes more force to open than you think it should, they’re totally correct!
The other big change is that I installed TLP in hopes of improving battery life. Using the default config out of the box seems to yield good results. However, this is just anecdotal evidence again, nothing scientific.
Otherwise, the general update is that this laptop continues to rock. I use it about 3-10 hours a week, including some intense 4 hour work sessions at the cafe. For full dev environment I run two vagrant VMs on Virtual Box along with Chromium, Firefox and PHP Storm as my IDE. I’m pretty sure I could get 6-8 hours of battery life running these apps if I was conservative with the screen brightness. Some times when I resume it, I’ll see 14 hours remaining in the battery life. It almost always drops down, but still neat to see.
It looks like you can still get this bad boy on eBay for just under $1,400!
8/13/2016 Update
I’m still totally loving this laptop! Seeing my wife get more comfy with her laptop and it’s touch screen, I wondered if I could find a fix for mine under 16.04. After some searching around a found a fix that is…so simple it’s silly. Quickly close and open the lid:
close the lid just to enter suspend state, but then reopen it quickly, so that it stays in suspend state even when the lid is open. Then press power button to wake it up. Then the touchscreen works again!
– xps9350: touchscreen stops working after sleep
After testing this over the last 4 days, I can confirm it works. Coupled with the fact that the OS and Chrome/Chromium handle single finger scroll and pinch to zoom, I’m a happy camper! The icing the cake was finding the Grab and Drag plugin for FireFox. Though pinch to zoom doesn’t work, single finger scroll does. Handy times!
11/24/2016 Update
One my fine readers pointed out that the touch screen under 16.04 has been more properly fixed. This is awesome! This gist on github has all the info you need. Be sure you read the part about using uname -r to get your kernel and make sure it matches on the line that the script is hard coded against. For it it was 4.4.0-45, but for the original author it was 4.4.0-47. As well, it didn’t fully start working for me until a restart.
5/17/2018 Update
Almost exactly two years in and this laptop is still my daily driver! It’s been *super* stable and I’ve had no problems with it. I’m still on 16.04, despite 18.04 having just been released. Also, check out my latest post about USB-C accessories I’m using!
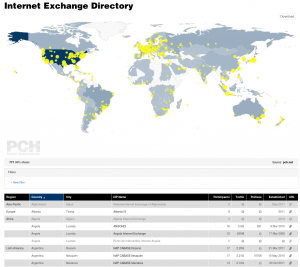 Version 1.1.1, the current version, was developed specifically so it could be used on PCH’s next generation Internet Exchange Point directory (IXP Dir). PCH’s IXP Dir was also the original use that MapTable was conceived for, so it has been a long journey until just now (as of Monday, July 25, 2016) that it has been pushed live! My main role as an employee of PCH was to complete the nascent integration done a while ago and ensure that all feature requests were made on GitHub so that the improvements would be made upstream of us for all to benefit from. It was great fun to do a deep dive into a well though out and highly function JS library.
Version 1.1.1, the current version, was developed specifically so it could be used on PCH’s next generation Internet Exchange Point directory (IXP Dir). PCH’s IXP Dir was also the original use that MapTable was conceived for, so it has been a long journey until just now (as of Monday, July 25, 2016) that it has been pushed live! My main role as an employee of PCH was to complete the nascent integration done a while ago and ensure that all feature requests were made on GitHub so that the improvements would be made upstream of us for all to benefit from. It was great fun to do a deep dive into a well though out and highly function JS library.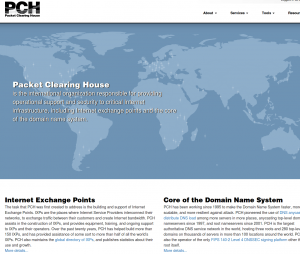 While I was in the IXP Dir, I also replaced the code on our home page which used an outdated version of MapTable. Fortunately, Simo had done PCH the huge favor of making one of the MapTable demo pages be based almost entirely on our home page. The ability to set an entirely custom color palette topped with icing on the cake of being able to specify an arbitrary SVG shape to use as markers on the map was just delightful!
While I was in the IXP Dir, I also replaced the code on our home page which used an outdated version of MapTable. Fortunately, Simo had done PCH the huge favor of making one of the MapTable demo pages be based almost entirely on our home page. The ability to set an entirely custom color palette topped with icing on the cake of being able to specify an arbitrary SVG shape to use as markers on the map was just delightful!