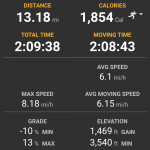
3 minutes, 53 seconds
A good friend of mine is setting up a new workstation in his new lab and wanted some advice on what would be the best setup. Being a bit of a geek about monitors and having set up my own desk, I had a lot of ideas on this. After a detail-packed email to him, I realized it’d make a great post for others looking to do the same thing.
The overall question I got: What would be the best standing desk with the best monitors for a new Mac Pro (nMP)?
This is fun! I get to spend imaginary money for a dream set up. For my “what’s the best” type of questions, I always try to refer to The Wirecutter, they’re great. As well, I try to use Amazon whenever possible for all of my shopping needs
The Desk
Though Wirecutter has a newer, cheaper recommendation, I still like their step up, the NextDesk Terra, which was their “regular” recommendation when I got mine. I see it’s now down to $1,500.
NextDesk upgrades: You can get a ton more bells and whistles including CPU stands, software integration, casters, batteries (for use when moving on casters) and more. The bare minimum I would get is the “Power Management,” which is really well done. Also – think on whether you want the hole(s) for cables in the desk. I regretted getting a single center one. I might have gone with none or two side ones.
Monitors and Stands
 I use Ergotron’s single and dual arm mounts. Amazon pictures the dual with two monitors on top of each other, but it can easily do two side by side (as well, they rotate for one portrait and one landscape). You can also order the single and then add a second arm to the same pole at a later date if you decide to add another monitor.
I use Ergotron’s single and dual arm mounts. Amazon pictures the dual with two monitors on top of each other, but it can easily do two side by side (as well, they rotate for one portrait and one landscape). You can also order the single and then add a second arm to the same pole at a later date if you decide to add another monitor.
IPS 60hz 4k displays used to be $3,000+. This is no longer the case! The Dell P2715Q 4k 27″ is down to $500! This is insane. You could get two of these no prob for your Mac Pro. IPS means that the viewing angles are perfect. 60hz means that the refresh rate is super fast and your mouse/window movements don’t feel sluggish.  4k means that you can either run HiDPI for super crisp text or 1:1 for TONS of real estate. Well, assuming you have good eyes for the 1:1 ;)
4k means that you can either run HiDPI for super crisp text or 1:1 for TONS of real estate. Well, assuming you have good eyes for the 1:1 ;)
Though 4k is ready for prime time, there are a few bumps in the road, specifically around displaying the boot process. As well, I see Apple’s nMP page boldly advertises “connect up to three high-resolution 4K displays.” However, I’ve also seen reports that the 3rd will be only at 30hz (boo!).
I forget which cables Dell comes with, but you can always get a 3, 6, or 9 foot (or more!); it’s nice to have the perfect length cable with no extra slack.  Same for ethernet, USB, firewire and thunderbolt cables too! For example, here’s a 6ft mini display -> display port cable for just $7. Oh yes – don’t use any ugly looking dongles! Get the right cable for the job.
Same for ethernet, USB, firewire and thunderbolt cables too! For example, here’s a 6ft mini display -> display port cable for just $7. Oh yes – don’t use any ugly looking dongles! Get the right cable for the job.
Mac Pro and peripherals
I don’t actually have a new Mac Pro (aka nMP aka 2013 Mac Pro), so I don’t have too much to say about which CPU and GPU to get. However, I did just get a 5k iMac that works great with the Dell 4k display! (Well, as long as you don’t mind some UI degradation. Ok, not so great, but worth the trade off for me.). To save money on the most expensive item in this monster desk setup, I strongly recommend using refurb.me – they’re the best way to effortlessly get good deals on Apple refurbed products! These are direct from Apple and include an Apple warranty.
 One new Mac purchasing trick I did learn is about buying your new Mac with more RAM direct from Apple. Don’t do it! For example, 64GB of aftermarket RAM only costs $664 instead of Apple’s $1,300.
One new Mac purchasing trick I did learn is about buying your new Mac with more RAM direct from Apple. Don’t do it! For example, 64GB of aftermarket RAM only costs $664 instead of Apple’s $1,300.  Consider putting the saved money toward more cores or disk or graphics card! I love Crucial for cheap aftermarket RAM, but I usually end up buying their stuff on Amazon. Here, B00GEC3ZJQ on Amazon is cheaper than the exact same part (CT5019226) on the Crucial site. Order two kits to max out your nMP to 64GB.
Consider putting the saved money toward more cores or disk or graphics card! I love Crucial for cheap aftermarket RAM, but I usually end up buying their stuff on Amazon. Here, B00GEC3ZJQ on Amazon is cheaper than the exact same part (CT5019226) on the Crucial site. Order two kits to max out your nMP to 64GB.
Keyboard and  mouse – I love Wirecutter’s recommendations for wireless versions of both mice and keyboards. They really add to the clean lines of VESA stands on the awesome desk.
mouse – I love Wirecutter’s recommendations for wireless versions of both mice and keyboards. They really add to the clean lines of VESA stands on the awesome desk.
Despite loving the wireless mouse and keyboard, my new boss got me a “welcome to your new job!” gift of a fancy Das Keyboard 4 Pro which I NEVER would have bought on my own given it’s price. If I had office mates, they NEVER would want me to use it because it’s too loud. That said, I actually love this keyboard so much that I alternate it with Wirecutter’s bluetooth pick, but the cable does ruin the lines of your desk. ;) Oh – I see it comes in “soft tactile” model as well. This might be a more quiet option!
 I love following this topic so drop me a note if you have any questions or want to update me with your experiences in this area!
I love following this topic so drop me a note if you have any questions or want to update me with your experiences in this area!