1 minute, 13 seconds
I’ve been using Tor quite a bit of late. It’s awesome!! I encourage you to check it out today. One of the drawbacks to using Tor is that some content deliver networks (CDNs) block traffic from the Tor network by default. For example, the way CloudFlare blocks Tor is to present a captcha for Tor visitors. The Tor blog had an interesting write up of this back in August of 2014.
Being a web developer, I’ve implemented many captchas and, specifically, reCAPTCHA which CloudFlare uses. Google has recently come out with v2.0 of reCAPTCHA which looks freakin awesome. That said, I think the “no captcha” term in that blog post isn’t quite accurate as you do have to click to prove you’re human in their v2.0 GUI.
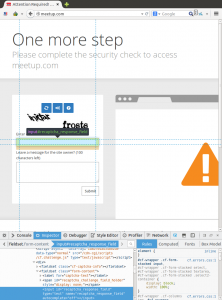
Today’s post, which falls clearly into the “rambling” category, is about CloudFlare’s implementation of reCAPTCHA. They’re using an early version, v1.0, on their site. If you look at the customizing reCAPTCHA guide for v1.0 it clearly spells out the changes you can make on how it looks:
You must state that you are using reCAPTCHA near the CAPTCHA widget.
Though CloudFlare has the question mark icon which links to reCAPTCHA, I don’t think it follows the proper branding guides.
To wrap up this ramble, I posit:
- CloudFlare should heed Tor’s advice on handling Tor traffic
- CloudFlare should properly attribute reCAPTCHA
PS – the astute, Tor using reader may note that I’m using an outdated version of the Tor Browser in the above screenshot. This has since been rectified ;)