1 minute, 23 seconds
As you may recall, around here we like our TLS, and we like it rare! I have no idea what “rare” means in the context of web encryption, but you know, that’s the way we like it! We also like it cheap! Even better than cheap (free) is open (libre)! So, put it all together, and you get Let’s Encrypt TLS certs on plip.com and related properties. Yay!
I saw the EFF/Let’s Encrypt crew speak at at DEF CON this past summer, and it was super inspiring. I’d already heard about the project, but it was that much more exciting to hear their talk. I was dead set on cutting over from my old CA, to the new, definitively open, one.
While I was in my server, I went and visited my fave site for 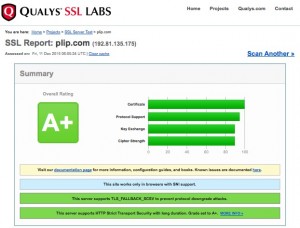 secure web server configs, cipherli.st. The only option I can’t run is SSLSessionTickets, as it requires Apache 2.4.11 or later. We’ll get there later with an Apache upgrade.
secure web server configs, cipherli.st. The only option I can’t run is SSLSessionTickets, as it requires Apache 2.4.11 or later. We’ll get there later with an Apache upgrade.
Put this all together? You get a big fat A+ on SSL Labs. w00t!
Some caveats are that Let’s Encrypt is just in public beta, so there’s some still some kinks to work out. For example, I mistakenly tried to get a cert for a wildcard vhost (eg “*.foo.bar.com”). I got back an error:
An unexpected error occurred: The request message was malformed :: Error creating new authz :: Invalid character in DNS name Please see the logfiles in /var/log/letsencrypt for more details.
So, while I shouldn’t have selected the domain to get a cert (Let’s Encrypt doesn’t do wildcard certs), the error was a bit cryptic. Fortunately the fine folks in their IRC channel (web IRC client – #letsencrypt @ Freenode to DIY) quickly pointed out to not use wildcards and that there was issue 1683 already open.
Awesome sauce, thanks Let’s Encrypt!